In the previous blog about LoRa, we discussed how LoRa is going to play a big role in the IoT market. Now we will go through some technical terms related to LoRa and LoRaWAN.
LoRa is a wireless modulation technique derived from Chirp Spread Spectrum (CSS) technology. LoRaWAN is a Media Access Control (MAC) layer protocol built on top of LoRa modulation. It is a software layer which defines how devices use the LoRa hardware.
LoRaWAN Network Fundamentals
LoRa is the physical (PHY) layer, i.e., the wireless modulation used to create the long-range communication link. LoRaWAN is an open networking protocol that delivers secure bi-directional communication, mobility, and localization services standardized and maintained by the LoRa Alliance.
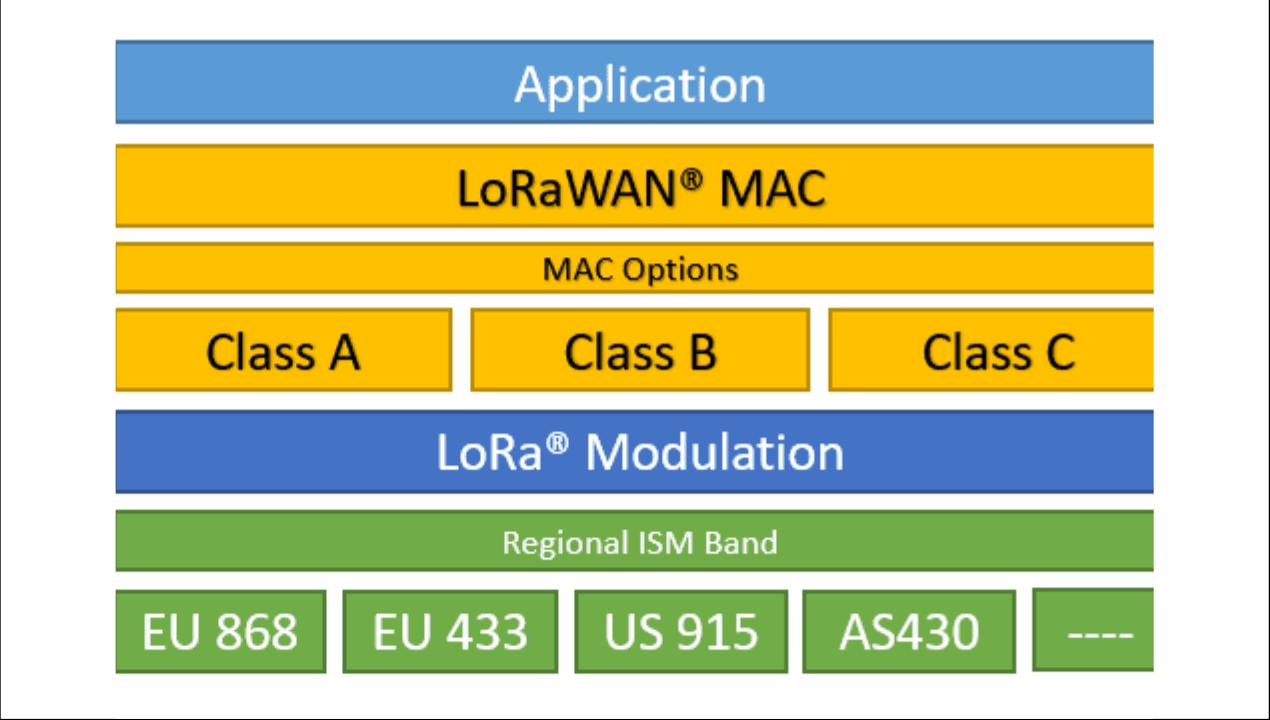
Elements of LoRaWAN network:
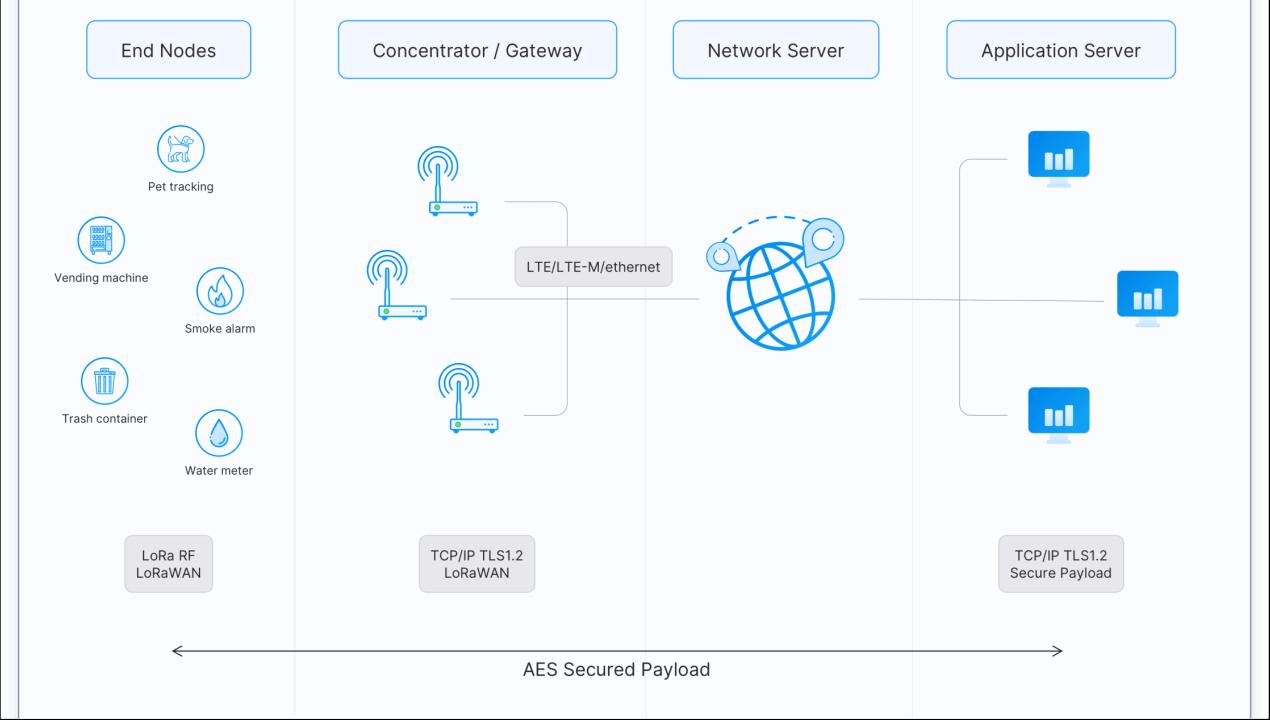
Now that we have a basic understanding of LoRa, we will examine the architecture of a LoRaWAN network.
End Devices: A LoRaWAN end device can be a sensor, an actuator, or both. They are often battery operated. These end devices are wirelessly connected to the LoRaWAN network through gateways using LoRa RF modulation.
Gateways: Each gateway is registered (using configuration settings) to a LoRaWAN network server. A gateway receives LoRa messages from end devices and simply forwards them to the LoRaWAN network server. Gateways are connected to the Network Server using Cellular (3G/4G/5G), Wi-Fi, Ethernet, fiber-optic or 2.4 GHz radio links.
Network Server: The Network Server manages gateways, end-devices, applications, and users in the entire LoRaWAN network.
Application Server: The Application Server processes application-specific data messages received from end devices. It also generates all the application-layer downlink payloads and sends them to the connected end devices through the Network Server.
Join Server: The Join Server assists in secure device activation, root key storage, and session key generation. The join procedure is initiated by the end device by sending the Join-request message to the Join Server through the Network Server. The Join-server processes the Join-request message, generates session keys, and transfers NwkSKey and AppSKey to the Network server and the Application server respectively.
Security:
Any communication technology dealing with many connected nodes need robust end-to-end security. LoRa achieve this by implementing security at two different layers: One for the network
One for the application Network security ensures authenticity of the node in the network and application security ensures operator does not have access to end user’s application data.
LoRa uses AES (Advanced Encryption Standard) security keys.
The specification defines two layers of cryptography Using a unique 128-bit network session key shared between the end-device and network server.
Using a unique 128-bit application session key (AppSKey) shared end-to-end at the application level.
These security features ensure that:
- Network traffic has not been altered.
- Only legitimate devices are connected to the LoRaWAN network.
- Network traffic cannot be listened to (no eavesdropping).
- Network traffic cannot be captured and replayed.
Conclusion
In this blog, we looked at the basic parts of a LoRaWAN network. We covered end devices, gateways, and servers that manage connectivity, applications, and security. LoRaWAN provides secure, efficient, and scalable communication for IoT setups. LoRaWAN is a strong choice for long-range, low-power IoT. Its solid design and AES encryption make it reliable.
Stay tuned for our next blog, where we’ll dive deeper into how LoRaWAN works in real-world use cases!
Similar Blogs
- LoRaWAN Technical Overview Part 1: IoT Connectivity Explained
- What is LoRaWAN? A Guide to Low Power Wide Area Networks
- LoRaWAN Technical Overview Part 3: Features & Advantages